This guide will describe the steps necessary to install and configure both the VPN Gateway and a VPN Client in a small test environment. Before getting started, you will need at least two computers and a network that supports Ethernet connectivity. One computer will act as a VPN Gateway and the other will act as a Windows VPN Client.
The Test Environment
Our test environment will model a single Client connecting to a Gateway that protects a small private network. The same Gateway can be easily redeployed in a production environment by changing the public interface parameters to match your real world configuration. The device acting as the VPN Gateway will need to support two network interface cards. The first will be referred to as the public interface and the second as the private interface. The VPN Client only needs to support a single network interface card that will provide connectivity to the public network.
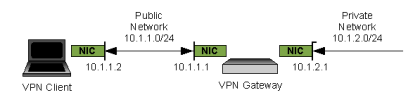
The IP address scheme chosen for our test environment is arbitrary. It is recommended that you connect the VPN Gateways private interface to your existing network and use valid private network address parameters in place of the parameters used in this guide. This will afford you the opportunity to perform more thorough testing between the Client and any private network resources you may wish to access. This should also allow Internet connectivity for your Gateway which may be necessary when performing some of the installation and configuration steps. At the very least, you need to make sure the Gateways private network interface has an active link status so it will respond to packets sent by the VPN Client.
Gateway Orientation in a Production Environment
In a production environment, the public network that the Client will most likely be connecting from will be the Internet. Depending on the size and complexity of your network, the VPN Gateway functionality can be provided by the same host that provides firewall protection or by a separate dedicated host. We will be using an Integrated Firewall and VPN Gateway for our test environment.
Integrated Firewall and VPN Gateway
For a small office, it is typical for an existing firewall to also be used as a VPN Gateway. This setup may be practical if the cost associated with maintaining additional hardware is undesirable.
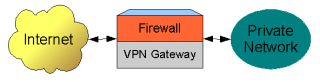
In this scenario, the Integrated Firewall / VPN Gateway device allows the private network to access Internet resources while also allowing VPN Clients to access private network resources.
Dedicated Firewall and VPN Gateway
For a larger office, it is typical for a separate dedicated Firewall and VPN Gateway to be used. This would prevent IPsec packet processing from degrading the Firewall performance and allow for a higher degree of security by enabling a separate host to filter packets between the VPN Gateway and the private network.
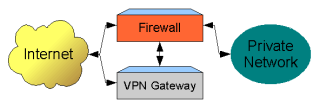
In this scenario, the Firewall allows the private network to access Internet resources. The VPN Gateway allows Clients to access certain private network resources by forwarding the traffic through the Firewall. In the event that the VPN Gateway is compromised, the Firewall will still have the ability to protect resources that need to remain private. Inbound access to the private network could be cut off completely while still allowing outbound access to Internet resources.