One of the challenges that face a VPN system administrator is keeping the Client configuration up to date when making a network change that may impact remote users. By using the Configuration Exchange, a VPN Gateway can provide dynamic configuration information to the Client during IKE negotiations. The alternative is to maintain a static Client configuration that will require user intervention if changes are required. This section describes some of the available configuration options and how they relate to client operation.
A Gateway can be configured to assign a private address and netmask to a Client. To support this, the Shrew Soft VPN Client offers two modes of operation that determine how private network traffic is sent to the VPN Gateway. The first is referred to as Virtual Adapter Mode and the second as Direct Adapter Mode.
Virtual Adapter Mode
When operating in Virtual Adapter Mode, the VPN Client creates a virtual adapter to use with IPsec communications. Local route management is used to ensure that packets destined to the remote private network will be sourced from the virtual adapter.

Direct Adapter Mode
When operating in Direct Adapter Mode, the VPN Client only uses the physical adapter for IPsec communications. Any private address assigned by the gateway will be ignored. Packets destined to the remote private network will be sourced from the physical adapter.

see also:
Configuring IPsec Tools : Network Configuration
VPN Client Configuration : Address Method
A Gateway can be configured to provide a Client with DNS and WINS configuration information. These parameters include DNS server addresses, a DNS default domain name, DNS split domain lists and WINS server addresses.
DNS Settings
By providing DNS configuration information, a Client will be able to resolve DNS names using a server located in the remote private network. This is useful when the DNS server hosts any number of private zones that are not resolvable using a public DNS server. A more advanced configuration would also provide a list of DNS split domain name suffixes. Using this list, a Client will only forward DNS requests to a private DNS server if they match one of the domain name suffixes. All other requests will be handled using the local DNS settings.
In the example shown below, the VPN Client is connected to a local network that has a DNS server that hosts the private local.com domain. It communicates with a remote network that has a DNS server that hosts the remote.com domain. If no DNS settings are supplied to the Client, it would be able to resolve the mail.local.com host name but not the mail.remote.com host name. If the remote DNS server setting is supplied to the Client, it would be able to resolve the mail.remote.com host name but not the mail.local.com host name. If the remote DNS server setting and a remote.com split DNS suffix setting are supplied to the Client, it would be able to resolve both the mail.local.com and mail.remote.com host names.

WINS Settings
By providing WINS configuration information, a Client will be able to resolve WINS names using a server located in the remote private network. This is useful when attempting to access a remote windows network resource using a Uniform Naming Convention ( UNC ) path name. The WINS server address would typically belong to a Windows Domain Controller or a Samba server.
see also:
Configuring IPsec Tools : Name Service Configuration
VPN Client Configuration : Name Resolution Settings
A Gateway can be configured to provide a Client with information that can be used to automatically generate a detailed security policy list. Using a policy list to selectively forward traffic to the VPN Gateway is referred to as Split Tunneling. The use of Split Tunneling can drastically reduce the amount of traffic processed by a VPN Gateway. It may also be required to allow a Client to access resources available from the local private network they connect from.
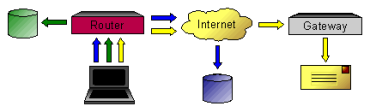
An example of a VPN Client that selectively tunnels traffic to the VPN Gateway.
If a Client is configured to obtain the policy information automatically from a Gateway but no information is received, all traffic will be forwarded to the Gateway as a last resort. Unless the Gateway and Firewall have been specifically configured to pass Client traffic back out of a public interface, a Client may have problems accessing Internet resources.
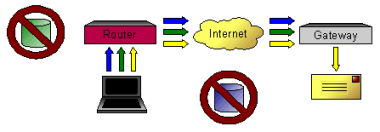
An example of a VPN Client that attempts to tunnel all traffic to the VPN Gateway.
see also:
Configuring IPsec Tools : Split Network Configuration
VPN Client Configuration : Remote Network Resources